Amazon.com: LOOYAR 32" PU Foam Medieval Crusader Battle Hammer Festival Props for Knight Warrior Costume Battle Play Halloween Cosplay LARP Silver : Clothing, Shoes & Jewelry
Tor'sHammer Attack on 192.168.1.9 IP with 5001 port number (see online... | Download Scientific Diagram
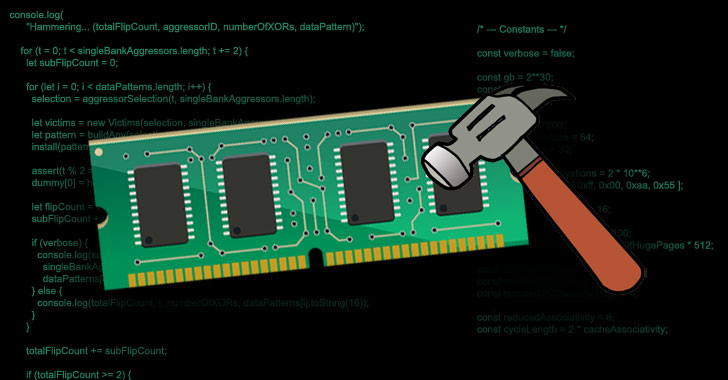
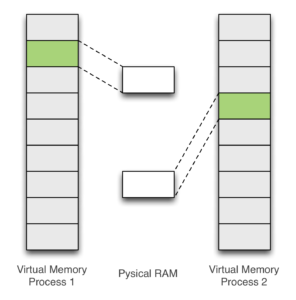
![Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium](https://miro.medium.com/v2/resize:fit:1400/1*RiU39j2IHVBTFyXRewDEew.png)











![Amazon.com: Hammer House of Horror: The Complete Series [Blu-ray] : Movies & TV Amazon.com: Hammer House of Horror: The Complete Series [Blu-ray] : Movies & TV](https://m.media-amazon.com/images/I/4181IGHYKRL._AC_UF894,1000_QL80_.jpg)